Cyber Security Company Kaspersky, Sparkcat, a malicious software, the gallery on the phone to the crypto currency wallets rescue sentences (Seed Words) found.
This was hidden in innocent applications such as malware, food order applications and artificial intelligence chat programs. SPARKCAT, which is estimated to affect 242,000 users, has victimized many people before being removed from the application stores.
What is Sparkcat? How does it work? How does it hunt crypto currency users?
Kaspersky revealed Sparkcat, a new malware targeting crypto investors. Experts have determined that this software is active in the App Store and Google Play as of March 2024.
Sparkcat analyzes the screenshots in the phone galleries with artificial intelligence -supported scanning methods and plays crypto wallet recovery sentences, passwords and other sensitive data stored here.
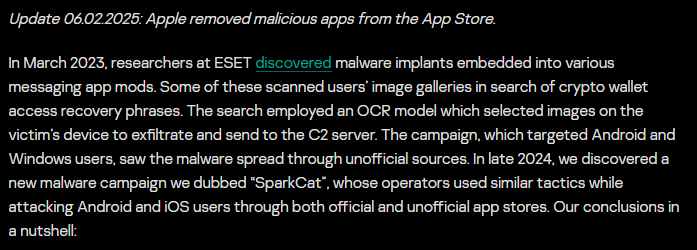
What applications have malicious software hidden?
Sparkcat was hidden in food order applications to deceive users, artificial intelligence chat assistants and other innocent programs. When users download these applications, malware automatically scanned the screenshots in the phone gallery and tried to seize crypto wallet information.
Although Kaspersky does not explain exactly how much crypto currency has stolen, the attack is targeted by users in Europe and Asia, and that there is strong evidence that it was from China.
Is it a new threat to the crypto currency sector?
Crypto fraud is often known for deceiving people with breast coin projects and investment promises carried out on social media. However, Sparkcat has adopted a different approach that targets the devices of privacy -oriented and directly.
According to Kaspersky’s research, Sparkcat was quite successful in overcoming security measures, but the attackers’ method of direct revenue could not be determined clearly. This shows that crypto investors should be protected not only from large -scale fraud projects, but also from hidden threats targeting personal data.